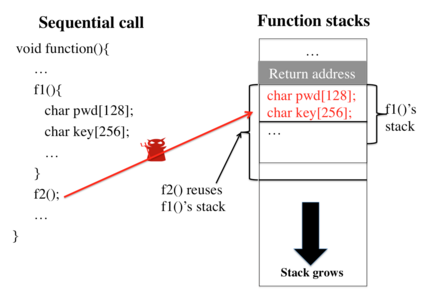
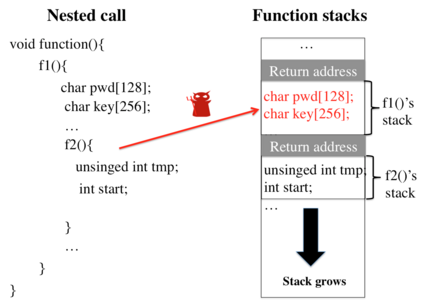
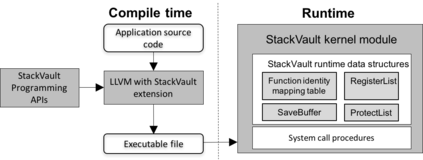
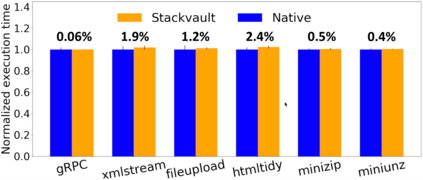
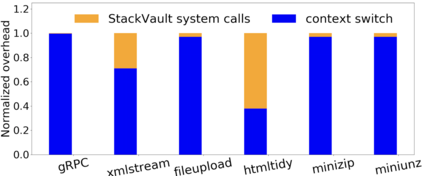
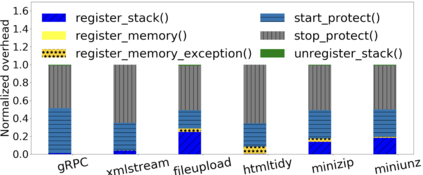
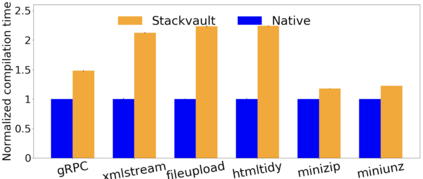
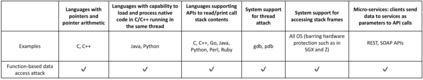
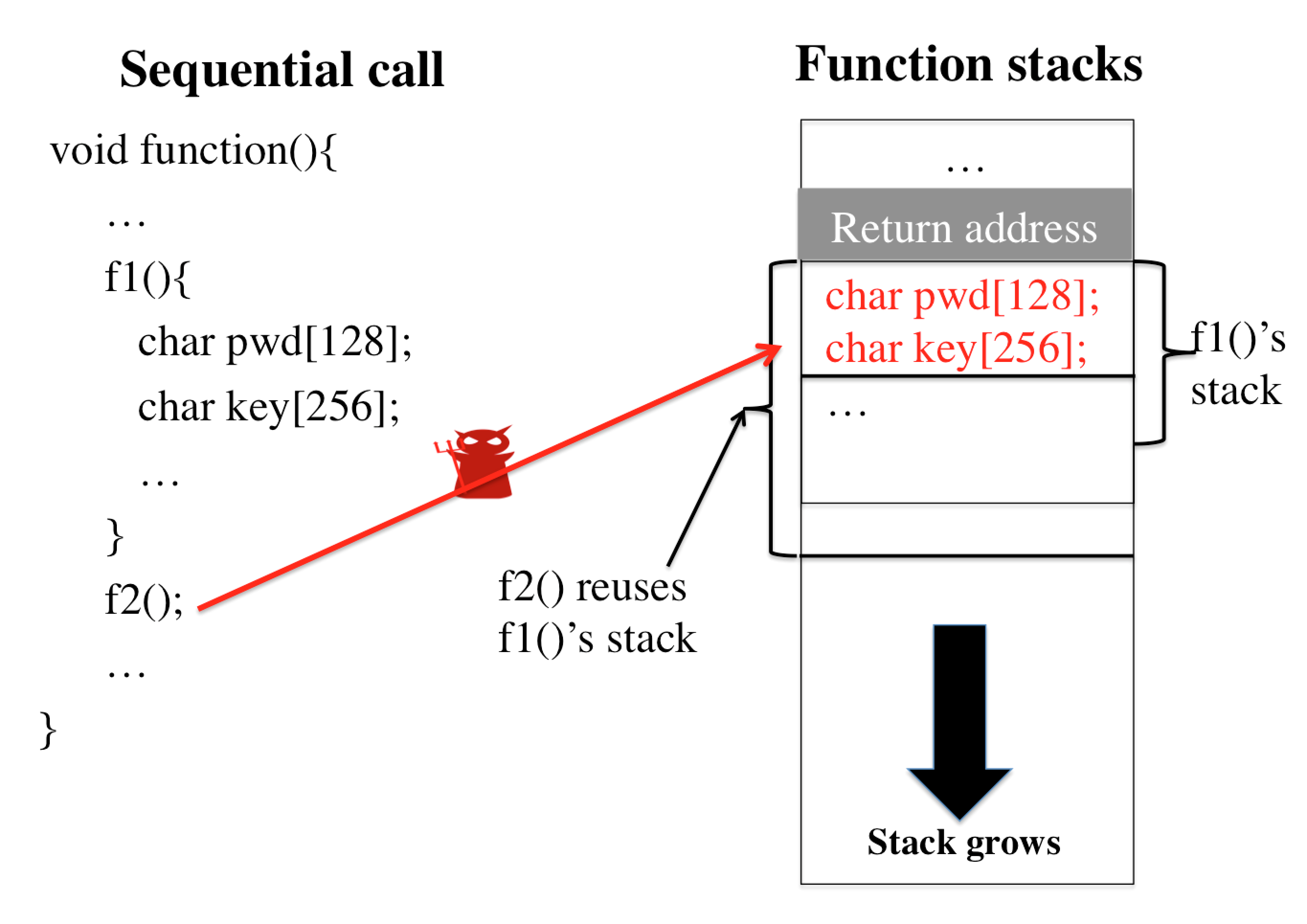
Data exfiltration attacks have led to huge data breaches. Recently, the Equifax attack affected 147M users and a third-party library - Apache Struts - was alleged to be responsible for it. These attacks often exploit the fact that sensitive data are stored unencrypted in process memory and can be accessed by any function executing within the same process, including untrusted third-party library functions. This paper presents StackVault, a kernel-based system to prevent sensitive stack-based data from being accessed in an unauthorized manner by intra-process functions. Stack-based data includes data on stack as well as data pointed to by pointer variables on stack. StackVault consists of three components: (1) a set of programming APIs to allow users to specify which data needs to be protected, (2) a kernel module which uses unforgeable function identities to reliably carry out the sensitive data protection, and (3) an LLVM compiler extension that enables transparent placement of stack protection operations. The StackVault system automatically enforces stack protection through spatial and temporal access monitoring and control over both sensitive stack data and untrusted functions. We implemented StackVault and evaluated it using a number of popular real-world applications, including gRPC. The results show that StackVault is effective and efficient, incurring only up to 2.4% runtime overhead.
翻译:最近,Equifax攻击影响到147M用户和第三方图书馆 -- -- Apache Struts -- -- 据称应对这一攻击负责。这些攻击经常利用敏感数据在过程记忆中未经加密存储,可由在同一过程中执行的任何功能进入,包括未经信任的第三方图书馆功能。本文展示了StackVault,这是一个以内核为基础的系统,以防止以内部处理功能未经授权的方式获取敏感堆叠数据。基于堆叠的数据包括堆叠数据以及堆叠点变量标出的数据。StackVault由三个组成部分组成:(1)一套编程API系统,使用户能够指定哪些数据需要保护,(2)一个使用不可靠功能身份可靠地执行敏感数据保护的内核模块,(3)一个LLLLVM编集扩展系统,使堆叠保护操作能够透明地进行。StackVault系统通过对敏感堆叠数据进行空间和时间访问监控和对堆叠变量进行数据控制,并不受信任地控制。 StackVaultVault a restal a lax Vlaftal a restime a laftal a restimal a resutal abal abal affotal abal affacts.